1Password CLI For Your ENV
I was listening to an episode of Syntax with Andrew Burkhart from 1Password, and they mentioned using the 1Password CLI for environment variables.
Somehow, I didn’t know this was a thing!
There has been a lot of talk about the best way to protect your private keys in the blockchain space when deploying contracts from your machine. My previous go-to was using cast wallet with foundry. While this works and keeps your keys out of your terminal history or .env file, using 1Password might be my new favorite method of securing sensitive information.
What Does Using 1Password’s CLI Look Like?
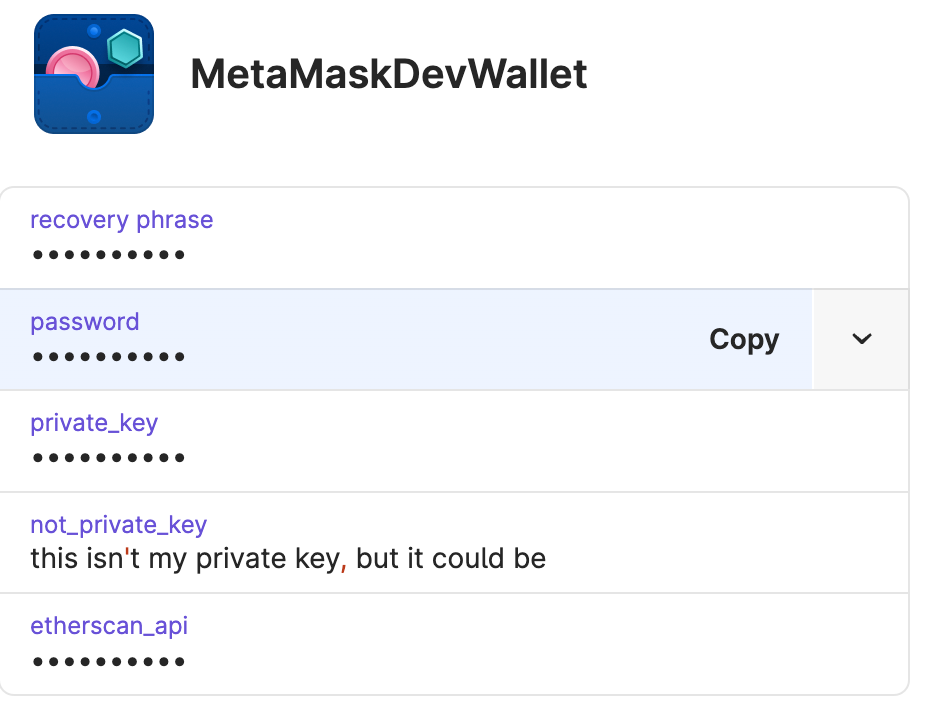
If you are familiar with 1Password, this will feel pretty normal. You create an entry, as you would for anything else. Here, you can see my not private key.
From the command line, you can read the values without ever exposing them.
A reference URI like op://development/MetaMaskDevWallet/not_private_key isn’t particularly sensitive. It’s no big deal to check that into GitHub or publish. This is great!
You can read them with the op CLI tool like so:
$ op read op://development/MetaMaskDevWallet/not_private_key
this isn't my private key, but it could be
Having experimented with this for all of one day, I think it will replace cast wallet going forward. This isn’t restricted to a single tool. Everything sensitive in your environment setup can now be securely accessed. Bravo, 1Password team!
Install The CLI
How do you go about getting this set up?
I’m on a Mac Laptop, so I’ll be using brew instructions for other OSes, which can be found in the getting started guide. I will also run through a quick example with foundry, but the same process should work for pretty much anything.
The first step is to install the 1Password CLI
brew install 1password-cli
You can check it’s installed by running op --version
If you haven’t already, create an entry for your wallet in 1Password
Build a basic foundry example
forge init hello_op
Clean things up for our example, removing the counter files and adding a couple of files for the NFT.
rm src/Counter.sol test/Counter.t.sol script/Counter.s.sol && touch src/NFT.sol script/NFT.s.sol && ls src script
Install the dependencies.
forge install Rari-Capital/solmate Openzeppelin/openzeppelin-contracts --no-commit
Import your keys
The power of 1Password CLI begins. The RPC URL is public; no need to worry about that, but here is what you can check in for your .env file. There would be no issue with this being in GitHub. PRIVATE_KEY and ETHERSCAN_API_KEY are a bit more sensitive though. I wouldn’t want to share them publicly. In this case, “op://development/MetaMaskDevWallet/private_key" is nothing to worry about sharing.
SEPOLIA_RPC_URL="https://ethereum-sepolia-rpc.publicnode.com"
PRIVATE_KEY="op://development/MetaMaskDevWallet/private_key"
ETHERSCAN_API_KEY="op://development/MetaMaskDevWallet/etherscan_api"
Prepare to deploy
Add the following to foundry.toml
[rpc_endpoints]
sepolia = "${SEPOLIA_RPC_URL}"
[etherscan]
sepolia = { key = "${ETHERSCAN_API_KEY}" }
Create scripts/NFT.s.sol
// SPDX-License-Identifier: UNLICENSED
pragma solidity ^0.8.13;
import "forge-std/Script.sol";
import "../src/NFT.sol";
contract MyScript is Script {
function run() external {
uint256 deployerPrivateKey = vm.envUint("PRIVATE_KEY");
vm.startBroadcast(deployerPrivateKey);
NFT nft = new NFT("NFT_tutorial", "TUT", "baseUri");
vm.stopBroadcast();
}
}
Deploy to the testnet
op run --env-file=".env" -- forge script --chain sepolia script/NFT.s.sol:MyScript --rpc-url $SEPOLIA_RPC_URL --broadcast --verify -vvvv
Let’s break down this command a bit.
op run --env-file=".env" essentially sources the .env file with the proper values. Then, after the --, we see our forge command which uses the imported values.
You will encounter a prompt to unlock 1Password.
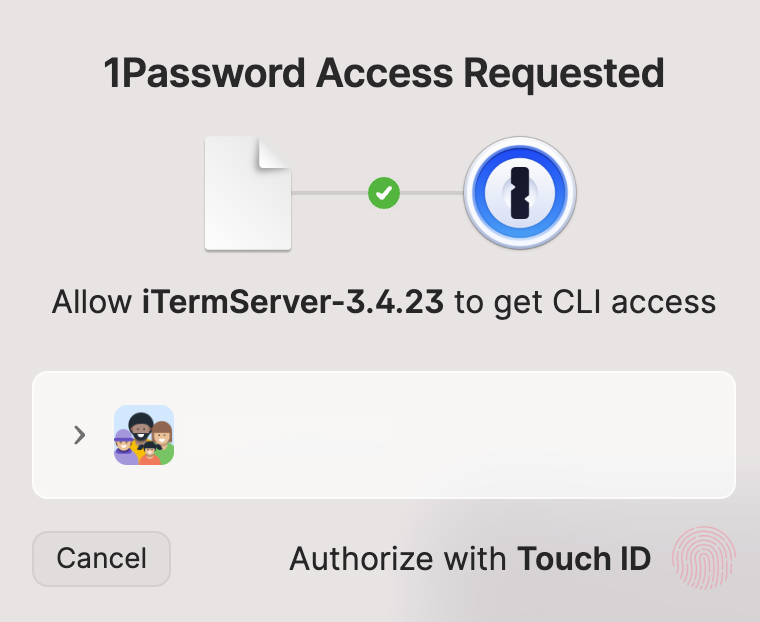
And that’s it! You have securely accessed your sensitive information. I’m excited to use this in the future!
Let me know your thoughts in the comments below.
Is this something you would use? Are there other tools I should be checking out?



